The end of April saw a double whammy of belt-tightening for many exporters as the Bureau of Industry and Security (BIS) imposed additional restrictions on the exports, reexports or transfers of specific goods, equipment materials or software to China, Russia, and Venezuela.
Changes Continue to Occur
Last week, we reported on the changes being addressed with the elimination of License Exception “CIV” to D:1 countries as BIS believes “the increasing integration of civilian and military technology development in these countries of concern made it impossible to retain a clear distinction between military and civil end users and end uses.” As indicated in our recent blog covering CIV changes, there will be an increased burden on exporters for items controlled for National Security Reasons (“NS”) to now obtain an export license that may or may not be approved dependent on the end user and the end use.
In addition to the elimination of the CIV License Exception, BIS moved to further tighten exports, reexports, and in-country transfer to China, Russia, and Venezuela but not all D:1 countries. BIS is clearly supporting the United States objectives with this final rule as it relates to national security and foreign policy outlined in the 2017 National Security Strategy (NSS) of the United States. The NSS initiative asserted that ‘China and Russia challenge American power, influence, and interests, attempting to erode American security,’ and that each country ‘supports the dictatorship in Venezuela and is seeking to expand military linkages and arms sales across that region.’
In an effort to deal with these threats, the new rule, now known as the ‘744 Rule’, takes effect on June 26, 2020 and will expand the licensing requirements for exports, reexports, and transfers of specific goods, equipment, materials, and software when an exporter has knowledge or has reason to know the items will be for Chinese, Russian, and/or Venezuelan military end users or end uses.
What This Means for Exporters
- Increased Due Diligence for Chinese transactions: Exporters must increase their due diligence with the evaluation of military end uses and military end users in China, particularly because of China’s extensive civil-military integration.
- What is a military end user?
- This now includes not only the national armed services, but also the national guard, national police, government intelligence, and “any person or entity whose actions or functions are intended to support military end-users.”
- This assumes that Chinese companies with diverse commercial and military businesses may be concerned “military end users,” which will mean increased licensing requirements.
- BIS suggests exporters will now need to reassess their due diligence methods relative to determining whether a customer has ties to a military end use and their tolerance for regulatory risk.
- What is a military end user?
- Expanded Scope of the “744 Rule”
- The new rule will expand the scope of those items subject to licensing for military end uses and military end uses.
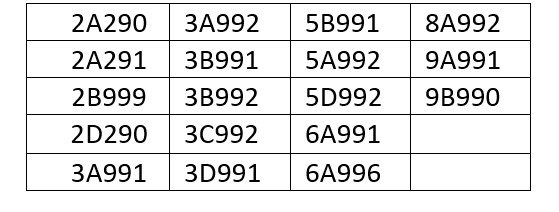
- This now includes the following ECCNs for goods, equipment, materials, and software:
-
- The above ECCNs are notable as they include common electronic, telecommunication equipment, navigational, equipment, certain aircraft and aircraft parts, and information security products that are not otherwise subject to export controls.
- Expansion of the Definition of “Military End Use”: The ‘744 Rule’ broadens the definition of the term “military end use” not only in China, but Russia and Venezuela as well. The new definition includes items for the use, development, or production of a military item; but also includes the operation, installation, maintenance, repair, overhaul, or refurbishing of such an item.
- This is a significant change as previously, the term ‘use’ was defined narrowly to mean all ‘operation, installation (excluding on-site installation), maintenance (checking), repair, overhaul, and refurbishing.’
- The broadened definition now identifies each element of the definition of ‘use,’ so that any one of the six elements, standing alone, is sufficient to meet the definition of ‘use’.
- Presumption of Denial: For exports, reexports, and in-country transfers to end-users/end-uses to China, Russia, Venezuela, the 744 Rule will increase the review standard under BIS from a case-by-case review to the presumption of denial.
- EEI Filing Requirements Expanded: One final note that adds another compliance layer- the ‘744 Rule’ also expands the Electronic Export Information (EEI) filing requirements for exports to China, Russia and Venezuela so that all exports to those destinations, regardless of values of the shipment (i.e.$2500 or more per Schedule B Number), must be accompanied by a mandatory EEI filing.
Exporters should be prepared to update their transaction review processes to include these changes in order to ensure they are not shipping to a prohibited end-use or end-user under the new definitions and rules. If you need assistance in determining how this new rule affects your business, please contact Export Solutions for a free consultation.
Beverly Demma is a Sr. Consultant for Export Solutions -- a full-service consulting firm specializing in U.S. import and export regulations.